Build AGC-compatible Forge apps
As part of the Atlassian Government Cloud (AGC) initiative, if you want your Forge apps to be available to our AGC customers, you'll first need to make your apps AGC-compatible. This tutorial will walk you through building an AGC-compatible Forge app.
You can either make your existing Forge apps AGC-compatible or create a new AGC-compatible Forge app from scratch. The difference between making an existing app and a brand-new app AGC-compatible is explained in the Create your app section.
Some instructions in this tutorial are workarounds. The Forge CLI is still under development for a better AGC experience.
Some Forge features are still unavailable on the AGC. See Feature roadmap for Forge for a complete list of supported and upcoming Forge features on the AGC.
Prerequisites
In order to manage your apps, you'll use the Forge CLI. There is no AGC-specific version of the Forge CLI, you'll use the same Forge CLI as for standard cloud Forge apps. You need to:
Also, you need to create an AGC account and obtain a test site: Get access to AGC.
Create an API token
In order to use the Forge CLI on AGC, you'll need an API token that is created inside AGC.
- Go to https://id.atlassian-us-gov-mod.com/manage-profile/security/api-tokens.
- Click Create API token.
- Enter a label to describe your API token. For example, forge-agc-api-token.
- Click Create.
- Click Copy to clipboard and close the dialog. Save the token in a safe place.
Override Forge CLI's API endpoint
In order to use the Forge CLI for AGC, you'll need to override an environment variable.
1 2export FORGE_GRAPHQL_GATEWAY=https://api.atlassian-us-gov-mod.com/graphql
Make a Forge app AGC-compatible
If you've built a Forge app before, you'll notice that the process for creating an AGC-compatible Forge app is largely similar. You may even notice that this tutorial has many similarities with our Build your first app tutorial.
Before we delve into the specifics, it's essential to clarify one key point. If you already have a Forge app in our standard cloud environment, there's no need to rewrite your application. Essentially, you'll be deploying the same app and code onto AGC.
Log in with the API token
This is similar to the standard cloud experience.
-
Start the process by running:
1 2
forge login -
Enter the email address associated with your AGC account.
-
Enter your AGC API token.
-
You'll see a message confirming you are logged in:
1 2
✔ Logged in as John Doe.
Work in progress
Forge CLI is still being updated with AGC-specific capabilities. For now, you can use the latest version of the Forge CLI with the FORGE_GRAPHQL_GATEWAY workaround. This will get simpler in the near future.
In order to use the Forge CLI with standard cloud systems again, execute unset FORGE_GRAPHQL_GATEWAY or set the environment variable to a standard cloud API endpoint and run forge login again.
1 2export FORGE_GRAPHQL_GATEWAY=https://api.atlassian.com/graphql forge login
Every time you want to switch the perimeter (standard cloud vs AGC), you need to remember to update the FORGE_GRAPHQL_GATEWAY override and run forge login.
Forge Remote in AGC
To use Forge Remote in AGC, your remote app will need to use a different set of URLS:
- When verifying remote requests from your AGC app, use the AGC JWKS URL:
https://forge.cdn.prod.atlassian-dev-us-gov-mod.net/.well-known/jwks.json - When accessing Forge storage from your AGC app, use the AGC Forge storage base URL:
https://api.atlassian-us-gov-mod.com/forge/storage/kvs
The AGC app will have a separate app ID from the standard cloud app. To handle requests from both environments, your remote server should check the app.id property in the Forge Invocation Token (FIT) to determine whether to use the AGC JWKS and storage URLs defined above, or the standard cloud environment URLs.
For general information about Forge Remote, see Forge Remote documentation.
Create your app
You may create an AGC-compatible app by registering an existing app or creating a new one from scratch.
Register an existing Forge app as AGC-compatible
Follow these steps if you already have a Forge app in our standard cloud systems and want to make it AGC-compatible.
-
First, you need to give a new app ID to your AGC-compatible app. Comment out the standard cloud app ID and add a new
idattribute with a different UUID to your app'smanifest.ymlfile. It should look like this:1 2
app: # id: ari:cloud:ecosystem::app/5c3ed5a5-721d-4fb8-b283-a3e22ec28d0a # Standard cloud app ID id: ari:cloud:ecosystem::app/b8703e30-dff5-409e-a0c1-cf4a6aa5e7f0 # AGC app ID -
Register your app by running:
1 2
forge register -
Enter a name for your app (up to 50 characters), for example my-agc-app.
-
Change to the app subdirectory to see the app files:
1 2
cd my-agc-appYou'll see a message indicating now your app is now registered in AGC.
1 2
✔ Registered my-agc-app
Work in progress
We're making additions to the format of manifest.yml to support perimeter (AGC vs standard cloud) overrides. Step 1 of this section is a workaround and won't be needed in the future. Until then, you must remember to switch the id field (uncomment one and comment out the other) every time you need to switch the perimeter.
Once we complete the changes, your manifest file will look like this:
1 2app: id: ari:cloud:ecosystem::app/5c3ed5a5-721d-4fb8-b283-a3e22ec28d0a # Standard cloud app ID perimeterOverrides: fedramp-moderate: app: id: ari:cloud:ecosystem::app/b8703e30-dff5-409e-a0c1-cf4a6aa5e7f0 # AGC app ID
When you run forge register, the perimeterOverrides section will be added and an AGC app ID will be assigned automatically.
Create an AGC-compatible Forge app from scratch
This process is the same as creating an app in our standard cloud systems.
-
Navigate to the directory where you want to create the app. A new subdirectory with the app's name will be created there.
-
Create your app by running:
1 2
forge create -
Enter a name for your app (up to 50 characters). For example, my-agc-app.
-
Select the UI Kit category.
-
Select the Confluence product.
-
Select the confluence-macro template.
-
Change to the app subdirectory to see the app files:
1 2
cd my-agc-app
The template you get will be the same as for a standard cloud app.
Deploy and install your app
This is the same as the standard cloud experience.
- Navigate to the app's top-level directory and deploy your app by running:
1 2
forge deploy - Install your app by running:
1 2
forge install - Select Confluence using the arrow keys and press the enter key.
- Enter the domain name for your test site. For example,
example.atlassian-us-gov-mod.net.
Similar to the standard cloud perimeter, you can deploy and install your AGC-compatible apps into development, staging or production environments with the -e or --environment parameter, for example:
1 2forge deploy -e staging
View your app
This is also the same as the standard cloud experience.
-
Edit a Confluence page in your test site.
-
Type
/. -
Find the macro app by name (
my-agc-app) in the menu that appears and select it. -
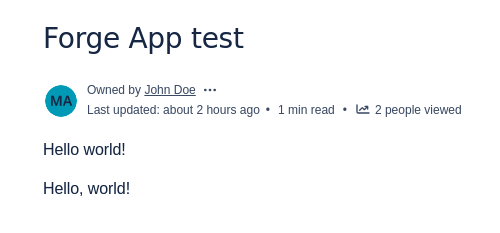
Publish the page. Your app is now installed on your development site. The app should display on the page like so:
Test/debug your app
AGC parity
Due to FedRAMP compliance requirements, forge tunnel isn't supported in AGC.
For daily development tasks, we highly recommend using our standard cloud environment, as the forge tunnel feature is unavailable in AGC. This approach offers a smoother and more efficient development process. Once your app is ready, you can proceed to deploy, install, and test it in AGC.
While we do not anticipate any issues, if you encounter problems in AGC that do not occur in the standard cloud environment, we suggest adding console.log statements to your code. You can then utilize the forge logs command or the AGC developer console to diagnose the situation.
As always, please don't hesitate to reach out to our support team whenever you need assistance.
View your app in the AGC developer console
You can view your AGC-compatible apps in the AGC developer console: https://developer.atlassian-us-gov-mod.com/console.
This console only shows your AGC-compatible apps. Similarly, you won`t see your AGC-compatible apps in your standard cloud developer console (https://developer.atlassian.com/console).
Once your app is deployed, it will appear in the AGC developer console. It offers the same user experience as the standard cloud developer console.
Distribute your app
See Distribute AGC-compatible Forge apps.
FAQ
Do I need to maintain a separate code base/branch?
No. Until we update the manifest file format to add support for perimeterOverrides, you'll need to comment and uncomment app IDs. When it comes to code, you should maintain a single code base for apps that are deployed in both standard cloud and AGC environments.
Do I need to obtain a FedRAMP ATO authorization?
No. Marketplace partners aren't expected to obtain a FedRAMP ATO authorization.
Do I need to deploy my app to the standard cloud environment first?
No, but we recommend you do so for development purposes. A Forge app can be deployed to the standard cloud environment, AGC, or both. However, since forge tunnel isn't available in AGC, we recommend that you deploy your app's development version into the standard cloud perimeter and do your daily development there. Once you've tested your app in standard cloud, you can deploy it to AGC.
Rate this page: