Cloud Fortified Apps Program approval process
Submit your Marketplace app
- Read all pages in the Cloud Fortified Apps Program documentation, including this page.
- Check you're eligible for the program.
- Start working on the requirements.
- When you're ready to submit a Marketplace app for approval, create a ticket at Developer and Marketplace support.
Track your submission
- After you've created a ticket, our team triages and reviews your submission for any missing or incomplete elements.
- We'll update you on your progress, and might ask you to clarify your responses, or update your submission in line with some requirements.
- For some requirements, such as security and support, we might need to verify the status of your Marketplace app. For other requirements, such as reliability, we might need to configure your Marketplace app, give accounts access to new views, and arrange test-runs of some of the processes.
Throughout this process, we use the workflow below to reflect where responsibility for the next step lies, and track the individual components of Marketplace app approval.
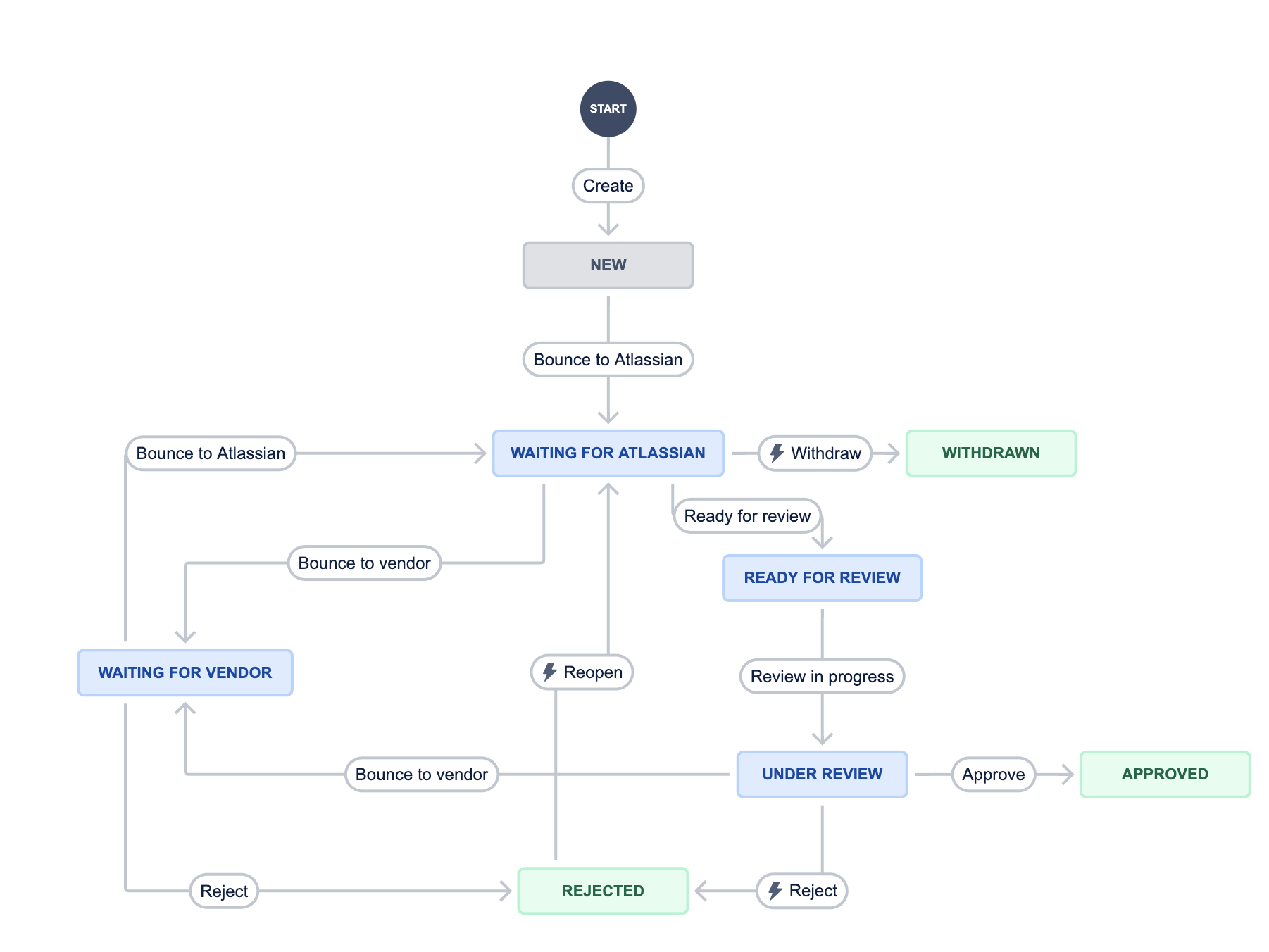
We endeavor to review and take your Marketplace app through the approval steps in a reasonable time. While we designed the process to avoid idle time, we're keen to learn and improve. Please note that some requirements, however, such as the security program requirements, inherently have some "soak" time before becoming active and approval can be granted.
After approval
-
Once approved, your Marketplace app is automatically updated in the Atlassian Marketplace to indicate the Cloud Fortified App badge. Your Marketplace app will also be included in a periodically updated list of Cloud Fortified Apps in go-to-market materials for our field teams and channel partners.
-
From time to time we might get in touch to gather feedback, share updates about any upcoming changes that we're exploring or plan to make for the program.
-
Your Marketplace app has an annual review process where we verify that your Marketplace app is in good order, and any new requirements are met. There is also an escalation process where Atlassian or customers can raise concerns about a Marketplace app's compliance with the program requirements.
Annual Review
Annual reviews take place each year during the last week of the month when your Marketplace app was first approved. For example, if your Marketplace app was approved for the Cloud Fortified program in March, your annual review will take place the last week of March.
We will reach out to you on the original approval ticket two weeks before your annual review begins, and then give you four weeks after the review to resolve any issues.
At this stage, during the annual review, we'll be verifying that the following Cloud Fortified requirements are being met:
-
Privacy & Security tab requirement: We'll check that all Privacy & Security tab fields are filled out and that any relevant changes to the Marketplace app in the past year have been reflected.
-
Support requirement: We’ll check that you have an up-to-date support contact listed.
-
Security requirement: We’ll check that you’re still participating in the Marketplace Bug Bounty program.
-
Other major changes: We'll request info on any significant changes (refer to the table below) that may impact the status of your Marketplace app's reliability or security posture.
In the future, if we add additional requirements to the list of annual review checks, we will notify partners in advance.
Action items for you
As long as you're continuing to meet your Cloud Fortified requirements, this review should require minimal action. The one required action for all partners is related to significant changes to your Marketplace app, listed below. During your annual review, on your Cloud Fortified ticket, we'll attach a form asking you if you've made any significant changes to your Marketplace app. We ask that you respond to this question in one of the following ways:
- If there aren't any significant changes to your Marketplace app: respond "NO" to the significant change question.
- If there are significant changes to your Marketplace app: respond "YES" to the significant change question and inform us of the changes and how they might impact the security or reliability of your Marketplace app by responding to the questions in the attached form. If you have made significant changes, we'll also check that you have updated your Marketplace app listing and Privacy & Security tab accordingly.
For Marketplace apps that don't meet the requirement criteria, a four week window will be provided to fix issues and satisfy the Cloud Fortified requirements.
What are significant changes
| Change | Examples of change |
| New, or significant updates to software libraries, platforms, or operating systems | Library versions that rely on deprecated security protocols or new open-source libraries if they result in changes to authentication. For example, updating a library in your Marketplace app such as OpenSSL to a new version that patches a known security vulnerability. |
| Addition or removal of subprocessors | For example, integrating a third-party service like SendGrid/Brevo for handling email notifications, which may process user email addresses. |
| Addition or removal of core app features | Adding a large new feature or series of features to your Marketplace app that potentially changes the way customers use the Marketplace app or discontinuing a primary feature of your Marketplace app drastically altering the Marketplace app's core functionality. For example, making significant changes to the Marketplace app's user interface, meaning that users need to re-learn how to use the Marketplace app, or removing a built-in document editor from a project management Marketplace app, affecting the way users interact with and use the application. |
| Changes to infrastructure or hosting platforms or services | Migrating your Marketplace app from a self-hosted server to a cloud-based hosting service. For example, moving your application from a self-managed server in your company's data center to a managed cloud service like Amazon Web Services (AWS), Azure, or Google Cloud. |
| Addition or removal of security controls | Introducing a new firewall to your Marketplace app's infrastructure. For example, implementing a new Web Application Firewall (WAF) like AWS WAF or Cloudflare in your Marketplace app's infrastructure. |
| Additions or modifications to cryptographic tools and services | Using a new encryption library to secure user data. For example, adopting a new encryption library like Argon2 or a similar library for hashing in your Marketplace app by replacing a less secure library. |
| Changes to any input validation mechanisms | Any changes to input validation mechanisms. For example, at the rendering stage, input sanitization should be performed to avoid XSS vulnerabilities. |
| Addition of new APIs or modifications to the existing APIs that could affect data accessibility or security | Authn/authz changes, encryption changes, new logging mechanisms, altering existing audit trails, changes to rate limiting, introducing or deprecating API endpoints in-scope. For example, deprecating an old API endpoint in your Marketplace app that exposes user email addresses and introducing a new one that only provides anonymized user IDs. This change would enhance user privacy and data security in your application. |
| Addition, modification, or removal of system monitoring capabilities | Switching from one error tracking system to another, altering the efficiency of error detection and resolution. For example, switching from an existing infrastructure monitoring system like Nagios to a new platform like Datadog. |
| Addition of new data stores or modifications to the existing ones | Upgrading or changing the existing database system in your Marketplace app. For example, moving from a MySQL database to a PostgreSQL database. |
| Changes to the Atlassian developer platform being used | Migrating the Marketplace app from Connect to Forge. |
Updates to program and requirements
We continue to develop and release improved developer tooling and guidelines on monitoring and improving the reliability and security of Atlassian Cloud apps. As we do so, we also update the Cloud Fortified Marketplace app requirements, documentation, and guidelines. We communicate these alterations ahead of time and release clear guides on how they should be adopted.
Rate this page: